About Crowdstrike
Secure The Endpoint
Safeguard USB
Managed Services
Resources

Primesys are proudly a
CrowdStrike Partner
About Crowstrike
CrowdStrike has redefined security with the world’s most advanced cloud-native platform that protects and enables the people, processes and technologies that drive modern enterprise.
CrowdStrike secures the most critical areas of risk – endpoints and cloud workloads, identity, and data – to keep customers ahead of today’s adversaries and stop breaches. The CrowdStrike Falcon® platform leverages real-time indicators of attack, threat intelligence on evolving adversary tradecraft and enriched telemetry from across the enterprise to deliver hyper-accurate detections, automated protection and remediation, elite threat hunting and prioritized observability of vulnerabilities – all through a single, lightweight agent.
With CrowdStrike, customers benefit from superior protection, better performance, reduced complexity and immediate time-to-value.
Primesys are proud to be a Crowdstrike Partner.
Secure the endpoint. Stop the breach.
State-of-the-art endpoint protection platform
Stop attacks — from commodity malware to fileless and zero-day threats, with an endpoint protection platform (EPP) powered by cutting-edge AI/ML. Elite threat intelligence, industry-first indicators of attack, script control, and advanced memory scanning, detect and block malicious behaviours early in the kill chain.
Stop cross-domain attacks
With unified visibility across cloud, endpoints and identities, correlate and detect cross-domain attacks to stop adversaries from moving laterally across your environments.
Advanced detection and response
CrowdStrike pioneered EDR delivering comprehensive coverage with a single platform, single console, and single agent — shutting down the most advanced adversaries in record time. A unique adversary-driven approach uncovers the most elusive threats with tactical precision, delivering high-quality, context-rich detections with minimal false positives.
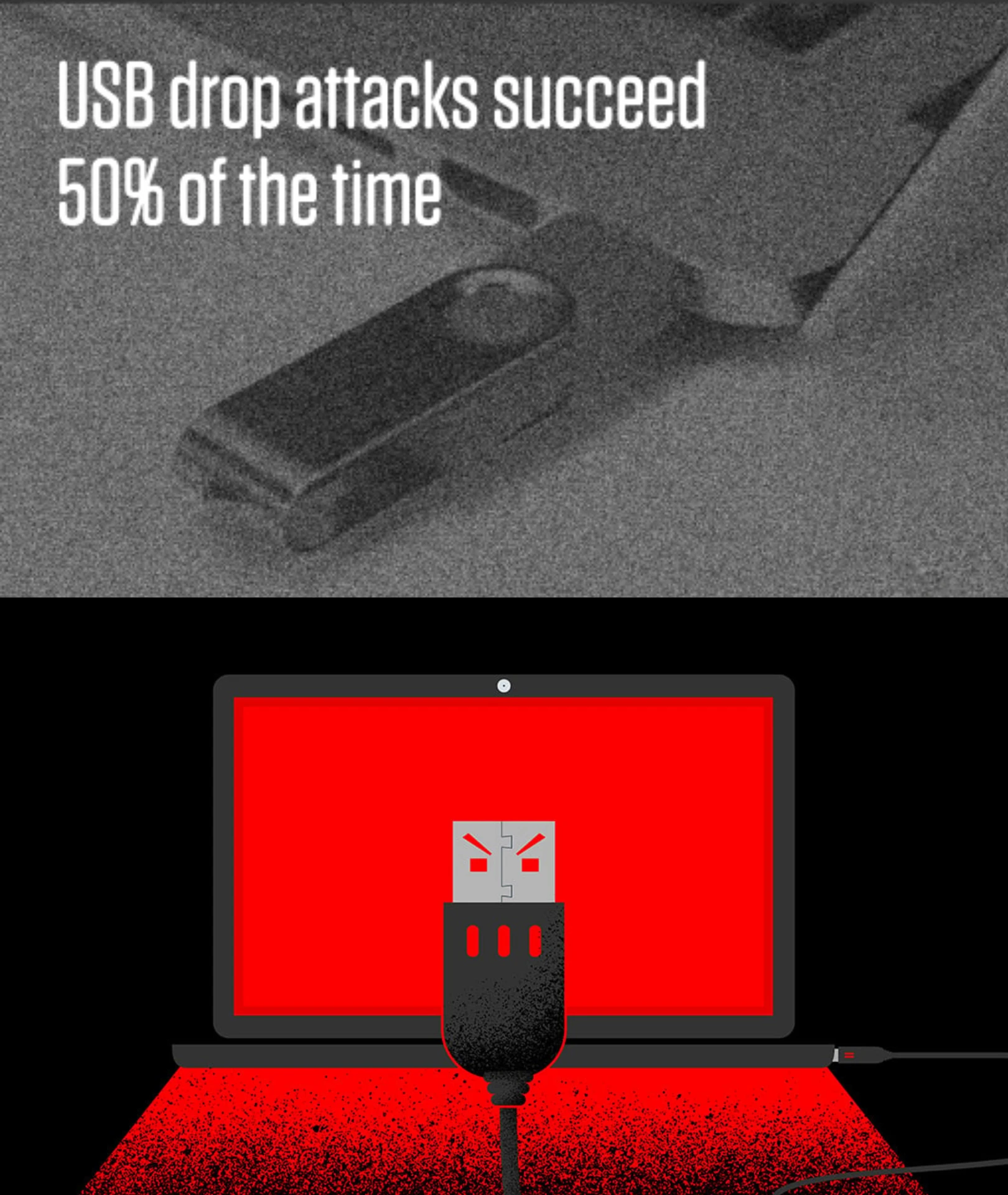
Take control of USB devices
Complete USB device visibility and control to safeguard your data and your business.
See all USB activity
View comprehensive file metadata and USB activity context to easily detect and investigate data loss and exfiltration. With detailed user and device information, ZIP archive introspection, and Microsoft sensitivity labels, you gain the visibility you need for a proactive defense.
Identify and safeguard source code
Detect source code movement with precision. Advanced machine learning watches over 40 source code languages, catching any sign of exfiltration. Simple, effective, and relentless — your intellectual property is safeguarded against threats.
Precise and granular control
Implement granular access rights to ensure only approved external USB devices are used. Simple workflows accelerate policy creation and allow analysts to test policy impacts prior to enforcement, eliminating potential disruption.

Go from under-resourced to undefeated
CrowdStrike Falcon Complete – Next-Gen Managed Detection & Response, with a 4 Minute Mean-Time-to-Detect (MTTD).
Level up your defence
Access world-class protection from the Falcon Complete team. Experts in incident handling, SOC analysis, and incident response tackle today’s toughest challenges with unmatched speed and precision.
Around-the-clock protection
Gain 24/7 monitoring for unwavering protection. CrowdStrike detect, disrupt, and eradicate advanced threats across all domains at speed and scale.
Know your adversary
Stop the breach with MDR, enhanced by Falcon Adversary OverWatch. AI-driven, intelligence-led threat hunting offers 24/7 coverage across endpoints, identity, and cloud workloads.
If you’re looking to partner with a Crowdstrike reseller, please get in touch.
Resources
Download the CrowdStrike Small Business Solution Brief here…
Additional Resources
Request Information
Request a Quote
Request a Free Trial
Request Information
Please use the form to request information about our Arcserve services.
Need Help?
CALL
01452 924202
info@primesys.co.uk
Request a Quote
Please use the form to request a quote for our Crowdstrike services.
Need Help?
CALL
01452 924202
info@primesys.co.uk
Request a Free Trial
Please use the form to request a free trial for our Crowdstrike services.
Need Help?
CALL
01452 924202
info@primesys.co.uk
Connected Services
Security for Networks,
Devices & Users



