What is Ordr?
Assets Details
Security Insights
Secure Automations
Audit & Report
Ordr
See every asset. Know your exposure. Secure and segment with automated policies.
Primesys are proudly an
Ordr Partner
About Ordr
Ordr is the Platform to See, Know and Secure All Devices.
The attack surface for enterprises continues to expand. Security teams are struggling with correlating asset data across multiple sources to identify security gaps, prioritize vulnerabilities, and respond to threats.
Ordr is the only purpose-built platform to discover and secure every connected asset. From traditional IT to the exploding growth of IoT, IoMT, and OT devices, SaaS and cloud, PrimeSys & Ordr have got you covered.
PrimeSys are proud to be Ordr Partner.

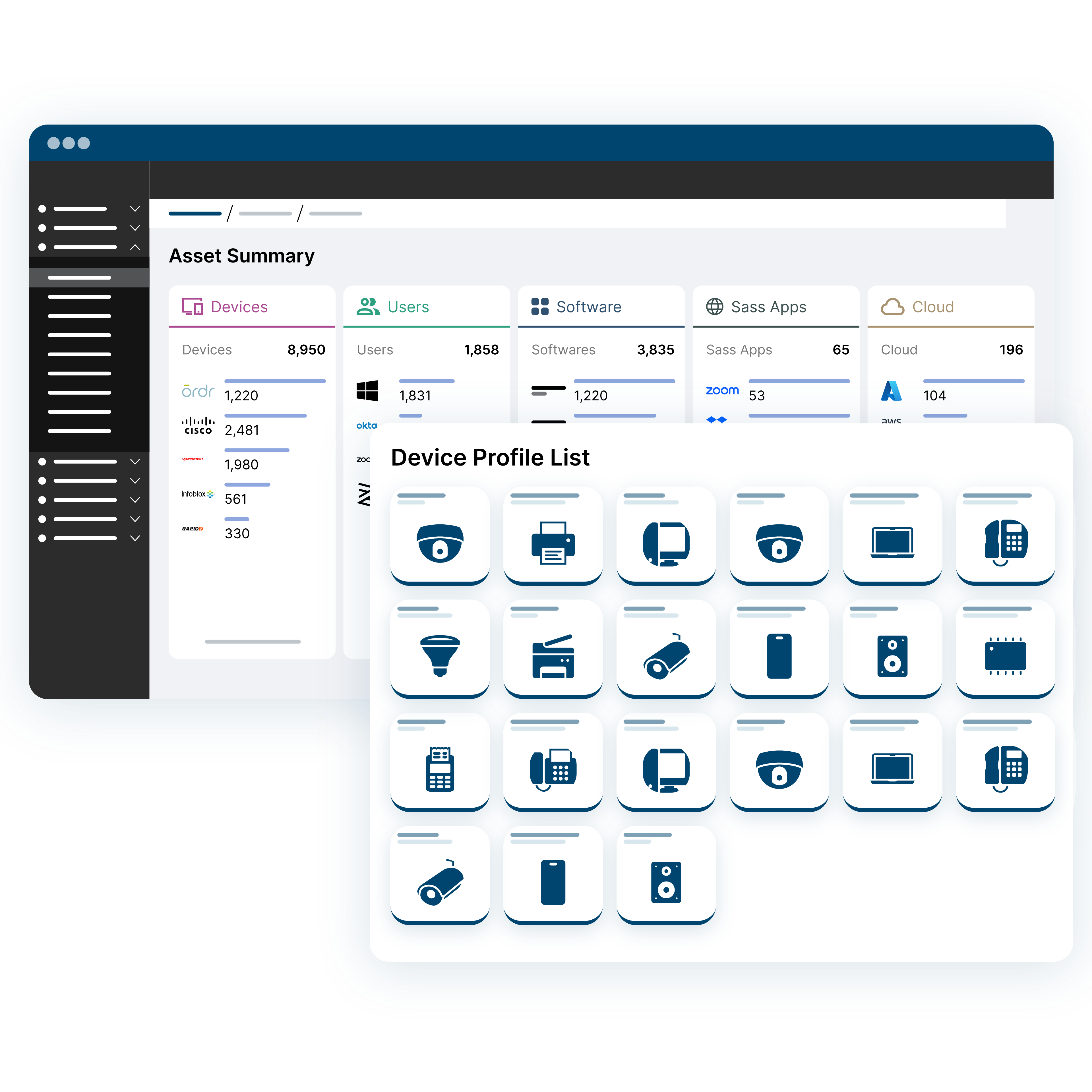
Granular Details of Assets
Gain a comprehensive view of every asset – devices, users, applications, cloud, SaaS:
- Visibility for all assets including the 40% of assets (IoT, OT, IOMT) that go unseen or unsecured
- AI/ML classification, de-duping and correlation for every asset
- Granular context including manufacturer, model, OS, connectivity, device owner, communication flows
- Generative-AI powered search answers complex questions about security
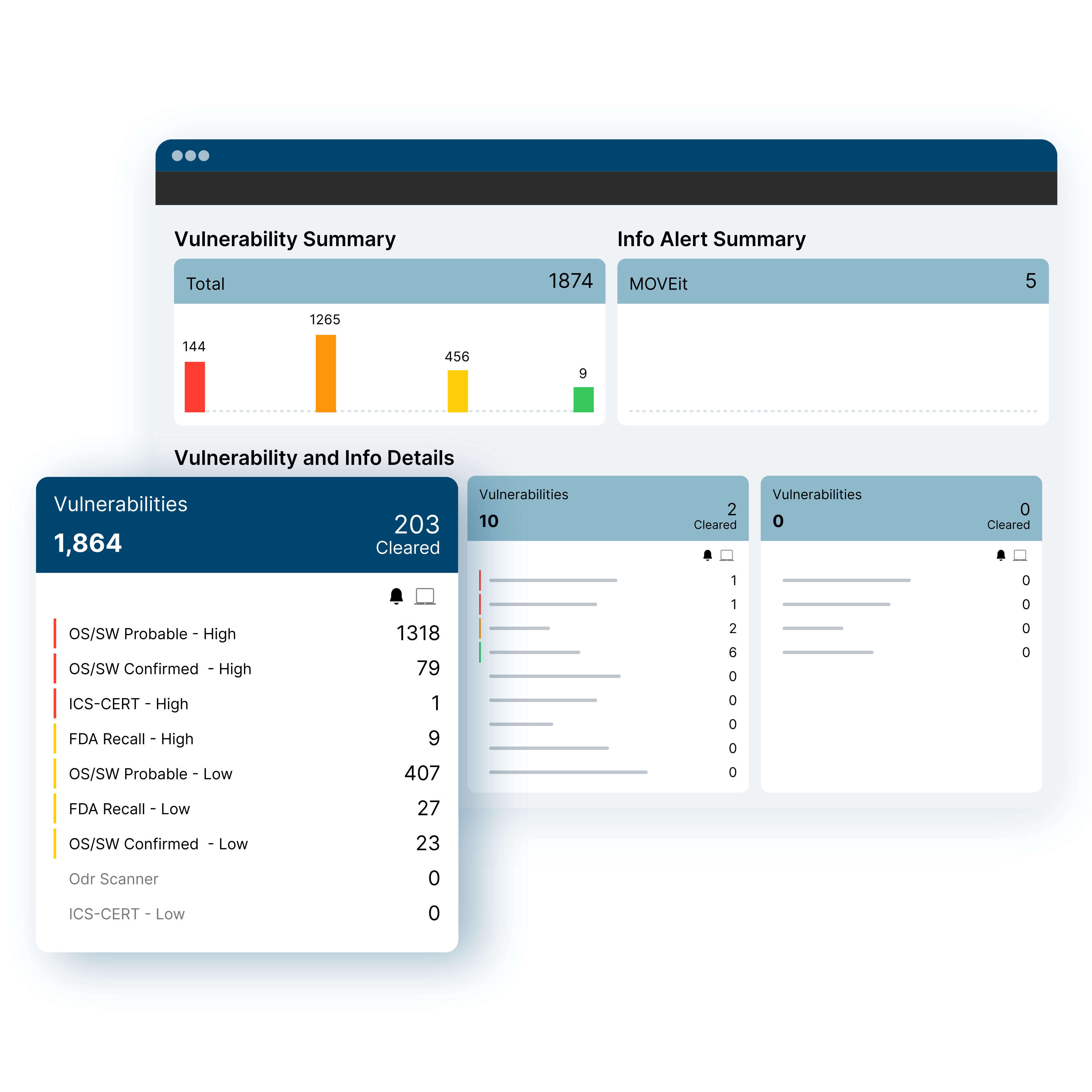
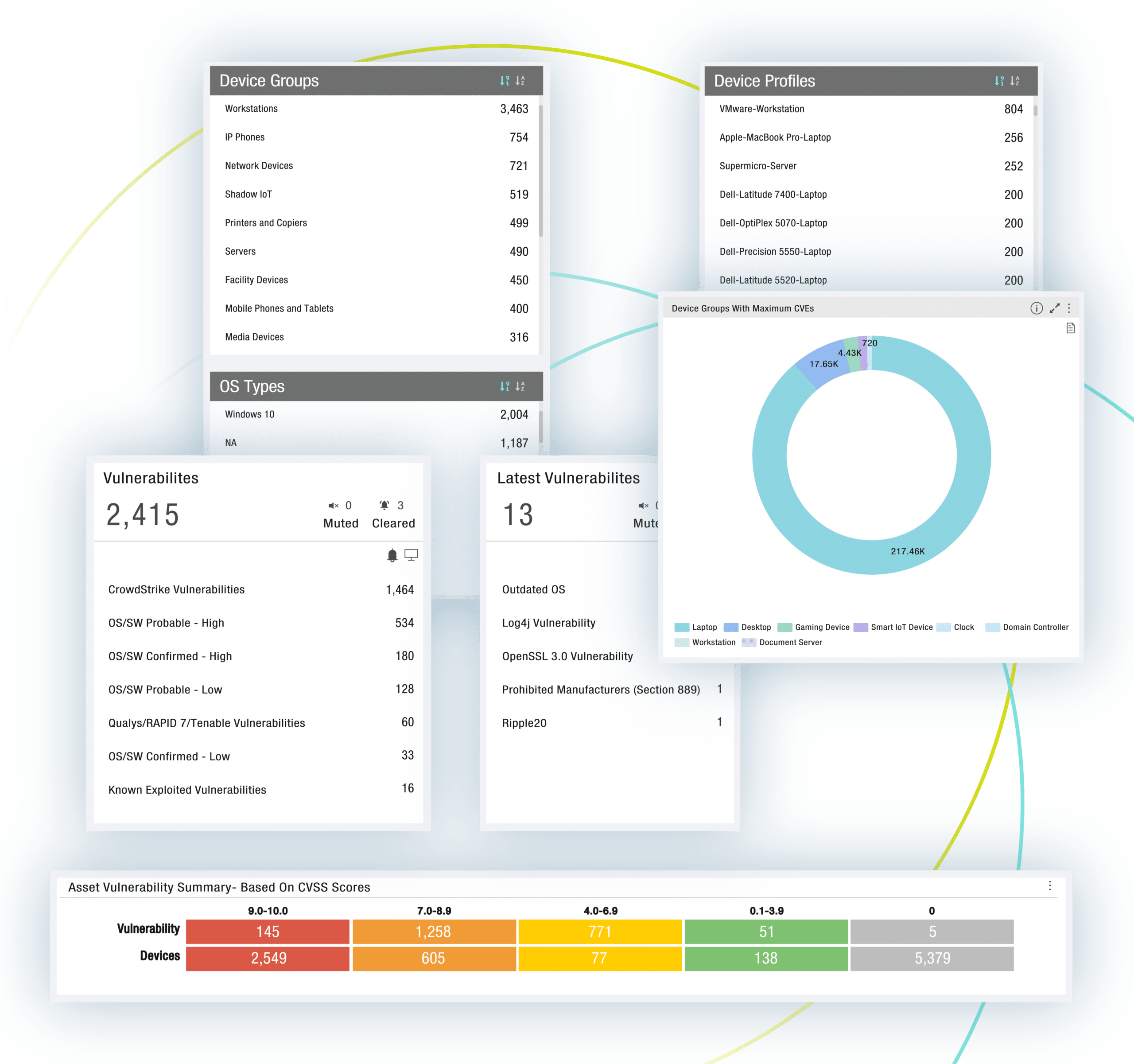
Security Exposure Insights
- Full lifecycle vulnerability management includes comprehensive vulnerability mapping for all assets, risk-based prioritization, and automated workflows
- Security coverage gaps such as devices with outdated OS or missing EDR/MDM agents
- Integrated IDS identifies known threats, attacker tools, risky communications (East-West and external)
- AI/ML engine baselines asset communications flows to surface devices behaving abnormally

Secure And Segment with Automated Policies
Integrate with existing tools to establish end-to-end workflows, enforce policies and enable Zero Trust segmentation:
- Generate tickets and alerts on ITSM and SIEM
- Enrich CMDB, CMMS with real-time accurate data
- Enrich vulnerability management solutions with vulnerability insights on IoT, OT and IoMT devices
- Automate security policies – block ports, terminate sessions, quarantine assets, move assets into different VLANs
- Generate Zero Trust segmentation policies to limit devices to “baseline” communications; enforce on firewalls, switches or NAC
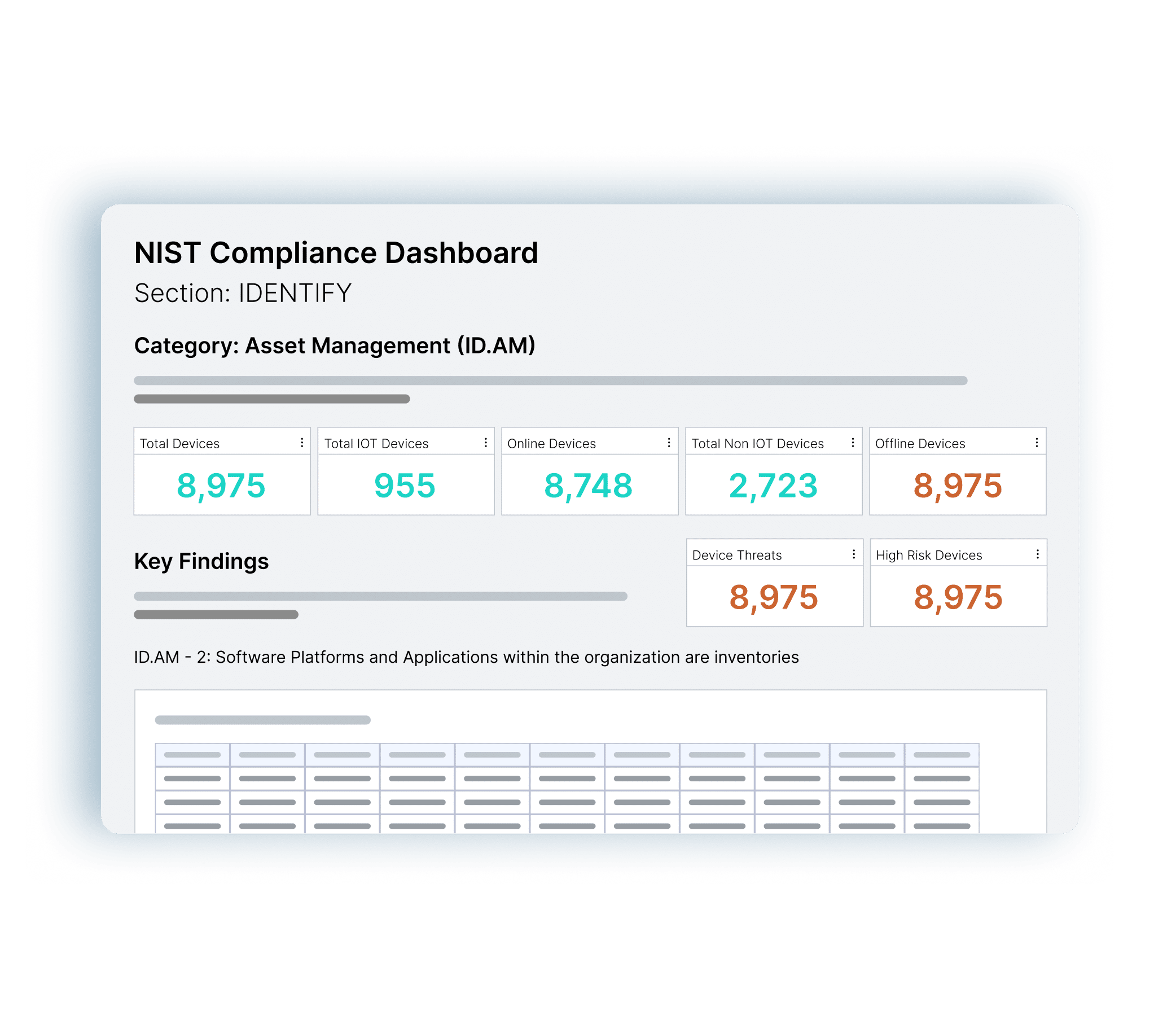
Audit and Compliance Reporting
Solve for today and tomorrow
Automate asset inventory and insights, to maintain compliance effortlessly by generating reports and comprehensive asset insights for standards like NIST, CIS Controls, Cyber Essentials, DSP Toolkit, CMMC, SOC2, PCI-DSS – and more. Dashboards and reports can be customized based on the business’s specific needs.
If you’re looking to partner with an Ordr reseller, please get in touch.

Resources
Download Ordr Overview Data Sheet here…
Request Information
Request a Quote
Request a Free Trial
Request Information
Please use the form to request information about our Ordr services.
Need Help?
CALL
01452 924202
info@primesys.co.uk
Request a Quote
Please use the form to request a quote for our Ordr services.
Need Help?
CALL
01452 924202
info@primesys.co.uk
Request a Free Trial
Please use the form to request a free tirla for our Ordr services.
Need Help?
CALL
01452 924202
info@primesys.co.uk
Connected Services
Wired, Wireless &
Wide Area Connectivity
Security for Networks,
Devices & Users